VPN (Virtual Private Network) has become an indispensable tool for privacy, data protection and remote access. MikroTik devices offer a wide range of functionality in terms of VPN configuration. This article will help you perform the necessary steps quickly and efficiently.
Why do you need VPN on MikroTik
The option is used in both business and home networks due to its ease of customization and extensive features.
The solution allows:
- Protect the connection when transmitting data over public networks.
- Provide access to corporate or home resources from anywhere in the world.
- Connect remote employees or company branches.
- Hide the real IP address to increase privacy.
These advantages make the use of VPN on MikroTik a popular solution for home and corporate needs.
Before starting the process, it’s important to make sure that:
- The device has access to the internet.
- RouterOS has been upgraded to the latest version.
- Connection information is present: IP, login, password.
By following the instructions provided, the procedure will go smoothly.
Configuring MikroTik VPN – algorithm of actions
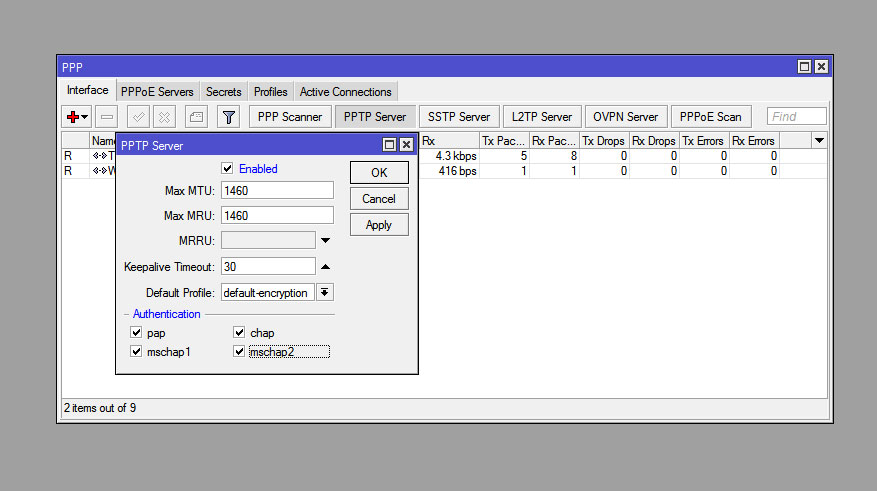
PPTP is one of the simplest protocols. It provides a basic level of security.
Start the PPTP server:
- Open WinBox, go to PPP → Interface.
- Add a new interface and select PPTP Server.
- Turn on the server, set the authentication parameters.
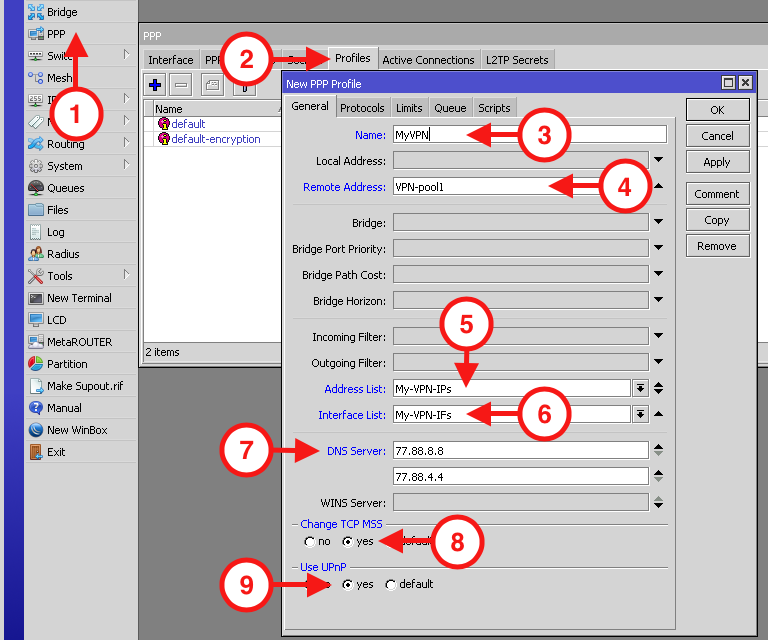
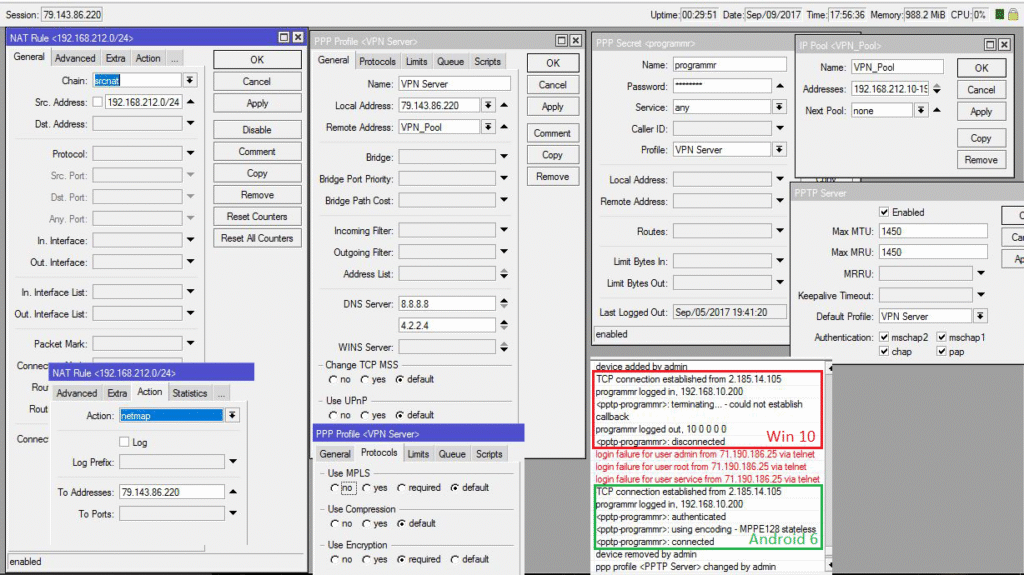
Next, in the Secrets section, add a user with login and password. Firewall configuration is required – allow PPTP traffic in IP → Firewall.
The L2TP option is more secure due to IPsec encryption.
Enabling the L2TP server:
- In PPP, select L2TP Server and activate.
- Install IPsec Secret in order to protect data.
Adding users. In PPP → Secrets, add accounts. Be sure to go to IP → IPsec and configure the encryption policy.
OpenVPN will require a specific list of actions.
- Create certificates. Use the built-in RouterOS or OpenSSL tool.
- Enabling OpenVPN. In PPP → Interface, create an OVPN Server, set the port and parameters.
- Users. In Secrets, add accounts with certificates.
Connect from a client device (PC or smartphone) and make sure the solution is stable. Setting up a MikroTik VPN is a reliable way to improve your network security and comfort.
Improved security and compliance with modern VPN standards
When configuring a MikroTik VPN, it is critical to consider your current encryption, authentication, and attack resistance requirements. Configuring a MikroTik VPN allows you to use several mechanisms to strengthen your defenses:
- Using IPsec with L2TP: This is the optimal balance between compatibility and security. The protocol is supported by most operating systems, and the presence of IPsec encryption greatly reduces the risk of interception.
- Disabling legacy protocols: PPTP, although easy to configure, is not recommended for use in a production environment due to vulnerabilities in GRE and MPPE. It is better to limit its access to test or temporary purposes only.
- Certificate-based authentication (OpenVPN): Certificate-based system provides the highest level of security and is convenient for centralized connection management, especially in large organizations.
It is also recommended to regularly update certificates and use complex passwords (minimum 12 characters with symbols, numbers and letters in different cases).
Manage routing and access policies through the VPN
Setting up a MikroTik VPN is not just about the access channel, but also about being able to fine-tune routing:
- Policy-Based Routing: MikroTik allows you to define which networks or devices can use the VPN channel and which can go directly to the Internet. This is useful if you want to differentiate access between company departments.
- Split Tunneling and Full Tunnel: To optimize load, you can use split tunneling – only certain resources are routed through the VPN while the rest of the traffic remains local. For maximum security, use Full Tunnel routing.
- Traffic Marking (Mangle): With IP → Firewall → Mangle, you can mark traffic by interface, port, or user and control its priority, route, and direction.
In this way, MikroTik VPN becomes not just a secure channel, but a full-fledged network segmentation and access control tool.
Monitoring and diagnostics of VPN connections on MikroTik
Effective VPN management is not possible without constant monitoring of connection status and quick diagnosis of possible problems. MikroTik offers built-in tools that allow the administrator to monitor the quality of VPN channels, detect failures, and get immediate information about connections.
What’s worth using:
- The PPP → Active Connections tab allows you to see the currently active VPN sessions, their duration and IP addresses.
- The
log printcommand and the Log tab provide insight into connection attempts, authentication errors, and channel instability. - Use Netwatch or scripts to ping remote addresses and send notifications when the VPN breaks.
- Built-in Torch and Traffic Monitor tools help analyze tunnel load and identify bottlenecks.
Such measures allow not only to control the current situation, but also to promptly respond to any tunnel failures.
Automate VPN management through scripts and Scheduler
MikroTik RouterOS supports process automation, which is especially useful when administering VPNs in distributed or rapidly changing networks. Scripts can perform actions based on time of day, resource availability, or channel utilization.
Automation capabilities:
- Automatic tunnel restart in case of connection failure (check via ping and subsequent reset of the interface).
- Enable and disable VPN on a schedule via the System → Scheduler tool.
- Changes the IP address or route interface depending on external conditions, for example, when the primary channel is switched.
- Email or Telegram notifications in case of connection errors or tunnel loss.
Automation saves administrator time and provides higher reliability of the VPN infrastructure without the need for manual intervention.
Practical application options for MikroTik VPN in business
MikroTik VPN in the corporate environment opens up a wide range of possibilities and increases the resilience of the IT infrastructure:
- Branch office unification: Through VPN, all offices and warehouses can be united into a single private network, providing centralized access to databases, CRM systems and IP telephony.
- Secure remote work: Employees can connect to the corporate network from laptops, tablets or smartphones, accessing internal resources without jeopardizing information security.
- IoT and surveillance camera support: VPNs are ideal for secure access to facilities with security or automation systems – especially if they are behind a NAT or ISP router.
Additionally, you can implement two-factor authentication (2FA) or a RADIUS server to increase control over external connections.